I've been working on my research proposal this past few weeks, and I am quite worried of the possible results from the informations I gathered. Actually, I've been to a confusion of my research procedures. I have been confused on the methods I would use in order to attain the results. I don't even know what to do.
No one, yes, someone who would guide me aside from sir RSG, no one (knowledgeable about research) helps me. So, difficult.... hahayyy...
Thanks to search engines, these online information database really is a great help! haha. They've been my best guide and buddy in my research proposal. Such a helper...
My topic, about VOIP. So new in the business industry. Not yet widely expose what it is, but yet widely in use. Users just not aware about it. They're using VOIP but not aware of it. I've observe the advertisement of GLOBE. The new 24ever advertisement, I think that product use VOIP. Phone-to-PC internet connectivity? hmmm? I think so... SO NEW!
So, I think that I will really have difficulties in this research of mine. But to the people close to me, Please do help and I badly need your guide and knowledge! hehehe
To my classmates, please comment to my research update thread if you have info or readings about my topic. it will be highly appreciated. Your names will be mention in my acknowledgment! hahaha...
Kidding aside, Let's look to the bright side. Let's pursue this research, and will gain knowledge...and additional infos...
good luck to my fellow researchers!
Friday, September 19, 2008
Analytical Framework
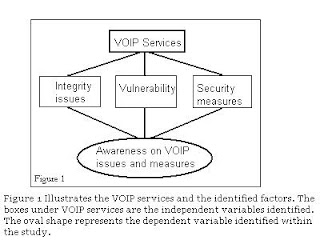
For more understandable illustration, please consider the figure 2 below:
Figure 2 shows the independent and dependent variables identified in the study. The box on the left identified the independent variables which were the VOIP service factors. The box on the right identified the variables dependent on the factors identified.
Research Methodology
Methodology
Research Design
This study would used descriptive and qualitative research method. According on the site (http://www.petech.ac.za/robert/resmeth.htm), “Descriptive research is thus a type of research that is primarily concerned with describing the nature or conditions and degree in detail of the present situation (Landman 1988)”. The emphasis is to describe, rather than to judge or interpret.
However, the researcher should observe the strict research requirement to acquire the possible results/output accurately.
According on the site (http://www.joe.org/joe/2002december/a1.shtml), “Qualitative research aims more at thoroughly describing a situation or explaining reasons for a problem or circumstance. It is typically thorough and provides in-depth understanding of a situation or group of people but does not attempt to quantify results”.
Thus, in the study to be conducted, it would merely describe the issues on VOIP services and the level of awareness of the chosen individuals in the community about the matter.
Research Instrument
The data in this study would be gathered through survey questionnaires to groups of people and a secondary data source through the data acquired from the World wide web and search engines.
Sampling technique
The sampling technique would be perform to the respondents knowledgeable or not about the study; but is aware of using the World Wide Web. The respondents could be working professionals and students of IT. The sampling would be intended to at least 50 respondents from either specified occupations.
Tuesday, September 16, 2008
VoIP Technology in the Philippines
The Philippines like no other nations, is a country manage to adhere with the fast evolution of technology even though it belongs to the third world of underdeveloped countries. It was just in recent times that VoIP was introduced in the Philippines.
In May of 2006, a deregulation bill was passed and was approved to the House of Representatives according on the site (www.voipcentral.org/entry/house-passes-voip-deregulation-bill-in-the-philippines/). The bill indicates that VoIP has been accepted and widely spreading in the country.
In September of the same year, MozCom released a product integrated with VoIP services which was known as ‘VCall’ according on the site (http://www. blogcrm.com/voip-in-the-philippines-killer-dude.php). Mozcom is the Philippines’ very first commercial ISP (Internet Service Provider), and received the license to operate VoIP service in August 2006 from the National Telecommunications Commission. The product integrates a web casting technology. In order to use the VoIP service, a user account must be established in http://www.vcall.ph/ site.
SMART communication, as one of the leading GSM network in the country has been engaged to VoIP to widen its communication service. According to Alec Barton in May 2006, SMART chooses Nortel’s international gateway solution to offer a wireless VoIP services to its consumer in the country and abroad. The gateway solution will increase the bandwidth efficiency and widen the network’s geographical contact (www.developingtelecoms.com/content/view/430/26).
VoIP technology in the country works in the contact or call center industry; to promote better solution in attend to the customer’s concerns. According to Roberto L. Bacasong, a Customer Interaction Associate which is locally known as ‘call center agent’, “It is no doubt that the Philippines is one of the leaders in using VoIP services, as the country is known to be the key leaders in outsourcing.” (http://ezinearticles.com/?VoIP-Technologies-in-the-Philippines&id=707232)
Call center industry is quite spreading in the country and yet the same with VoIP technology. Sooner, VoIP services would be widely applied in home and businesses in the Philippines.
VoIP phone VS. Traditional Phone
For many years until the present, traditional phone which is commonly called telephone, was widely use in businesses and households. But recently, it has been phased out by the technology and features offered by the VoIP.
VoIP is better than a telephone in features and application. A telephone is only used for call connection to other telephone. It has directory lists of telephone numbers of the telephone subscribers. Better yet, cost is payable monthly depending on the type of call; if it is local or a long distance call. When doing a landline call, area code is added for local or national call and in long distance calls. Calls made can only be occupied by one caller at a time.
While in VoIP, calls can be made to any mobile numbers, to the same VoIP phone or through the computer. Some VoIP providers allow user to use traditional phone but with the use of adaptor. Costs are also the same of that of the traditional phone but with the additional monthly bill for the broadband service. VoIP has no directory assistance and no access to emergency call number unlike the traditional telephone. VoIP can take up many phone calls; and there is no need for the recipient to answer all the calls.
Telephone conversation with VoIP is more efficient and cost saving than those of the traditional telephone. Many VoIP providers offer services which can be less of charge than the usual telephone charge.
Integrity, Vulnerability and Security in VoIP
Integrity of VoIP
VoIP phones and infrastructure are connected to the internet through routers and servers; and is accessible by the availability of electricity or any power generator. In occurrence of power outage, connections between networks can fail. In this instance, VoIP providers arrive into using Uninterrupted Power Supply (UPS) to maintain electricity; but with the length of time of availability.
According on the site, (http://en.wikipedia.org) to deal with VoIP’s power dependency, VoIP providers needs to improve there connectivity through backup DSL and providing UPS or power generator on the site where VoIP are present.
Further, VoIP call is executed by sending voice over the internet; the conversation is broken up into packets. Then the packets are sent over the same network. This procedure could lead the network to congestion and Denial-of-Service. When this occurs, VoIP can be vulnerable to DoS attacks and threats; and attackers may take the opportunity to interfere in the conversation.
According to Paul Curran, calls could be corrupted by interrupting the RTP (Real-time Transmission Protocol) packets and changing the contents or execute delay into the call before it is received by the recipient (http://www.microsoft.com/uk/business/ security/VoIP.mspx). This may result to the disruption of VoIP call integrity.
To maintain integrity in VoIP, message or packet should be authenticated; and the packets should retain its content unchanged. Phones with caller ID should reveal the identity of the caller and calls should be recorded and guarded. If not so, the phone number can be hacked and used as a stolen account with the calling bills at the victim’s expense.
According on the site, (http://www.frost.com/prod/servlet/market-insight-top.pag? ocid=42936783) DoS attacks can be prevented by protocol tuning, buffering, configuring tags and port blocking. VoIP providers should provide failover session control service for backup in case of network failure or if the network is under Denial of Service. Authentication of network elements, such as the packet and message, can make the hackers difficult to interrupt in the conversations. The user needs to improve the communication security to lessen the threat occurrence.
With strong security build-up over the internet connection, it has less opportunity for the VoIP to be hacked.
Vulnerability of VoIP
"VoIP networks are known to be particularly susceptible to DoS and Distributed DoS attacks," says Butler Group Senior Analyst, Andy Kellett. "The convergence of voice and data networks means that successful virus-based attacks could be used to bring down the entire business with both voice and data channels potentially being paralyzed by a single attack model.” (http://www.microsoft.com/uk/business/security/VoIP.mspx)Convergence of voice and data networks makes the VoIP organizations cost efficient and process improve in the services they offered.
The susceptibility of VoIP through Denial of Service attacks and other threats is due to the organizations which install VoIP services which focus of the deployment of service is the throughput and the quality of service; and security of service is just the second option.
According to the Internet Security System in their article on “VoIP White Paper”, the quality of service is and always be an important component of voice transmission whether in analog or digital form. However, it must be realize that VoIP is also a data to be transmitted. To be able to transmit, the voice and message will be broken into packet first before being sent over a network; and this procedure is highly susceptible to number of attacks.
The primary types of attacks commonly associated with the vulnerability of VoIP are the following:
1. Theft of service which also known as ‘Toll fraud’
2. Eavesdropping
3. Impersonation
4. Phishing
Aside from these major attacks in VoIP, there are also other types of attacks according to the Internet Security System (ISS):
1. Call Re-direction
2. Information theft
3. Call Integrity compromise
Further, VoIP service is open and available as much as the connection with the broadband is highly present. Because of service availability, some attacks to VoIP could also be encountered, such as the:
1. DoS or Denial of Service Attacks
2. Spamming
3. Internet Virus
4. Worms
5. Hacking
In addition, since VoIP is vulnerable to all problems associated with broadband services, the vulnerability could affect the call quality in VoIP. This quality can be identified as the following according on the site (http://communication.howstuffworks. com/ip-telephony11.htm):
1. Latency
2. Jitter
3. Packet Loss
Because of these threats and attacks, phone conversation become corrupted, distorted and lost due to transmission errors. In order to deal with these, internet stability and strong security should be guaranteed and provided.
Security in VoIP
When conversation is performed, a session between caller and recipient is being initiated. According on the site, (http://www.securiteam.com/securitynews/ 5MP0C00GAM.html) the network layer that holds the session is the Session Initiation Protocol (SIP) which is responsible for creating, modifying and terminating sessions either with one or more participants.
According to the researchers of Royal Institute of Technology in Stockholm, Sweden, only few users of VoIP with SIP based telephony pay attention to call security. Most users overlook on how vulnerable VoIP service can be. Users of VoIP services today are primary concerned to the quality of service such as voice quality, latency and interoperability. But some security organizations, like ISS, are sending cautions to users about the dangers brought by unsecured VoIP services.
However, in order for VoIP to be adopted globally in the market, security facilities must be provided to address the worst security vulnerabilities of VoIP. "VOIP security needs to be handled in the overall context of data security," Krauthamer says, director of IT at Advanced Fiber Communications Inc. (AFC), a Petaluma, Calif.-based manufacturer of telecommunications equipment. AFC is using limited VOIP communications according to the article of Jaikumar Vijayan in the site (http://www.computerworld.com/).
But according to Maxine Kincora, “VoIP security measures won’t stop hackers”. (http://searchcio.techtarget.com) Because of VoIP’s vulnerability and unreliability, hackers were able to spread attacks in VoIP. Consumer could take cautions in order to protect their network from being susceptible to attacks and hackers. The other technologies could be protected basically; but with VoIP, no one is doing such protection.
However, there are things to consider in making secure VOIP which were the following according on the site (http://voip.about.com/gi/dynamic/offsite.htm):
1. Using of Firewalls
2. Enforcing Authentication
3. Using Encryption
4. Secure Service Provider
Security issues were the challenge for VoIP network, there are other steps to protect and prevent VOIP network from attacks according on the site (http://www.voiplowdown.com/2007/ voip-security-challenges-25-ways-to-secure-your-voip-network):
1. Restrict all VoIP data to one Virtual Local Area Network (VLAN)
2. Monitor and track traffic patterns on your VoIP network
3. Lock down your VoIP servers
4. Use multiple layers of encryption
5. Build redundancy into VoIP networks
6. Put your equipment behind firewalls
7. Update patches regularly
8. Keep your network away from the Internet
9. Minimize the use of softphones
10. Perform security audits on a regular basis
11. Evaluate physical security
12. Use vendors who provide digital security certificates
13. Secure your gateways
14. Manage servers separately
15. Sort SIP traffic
16. Examine call setup requests at the application layer
17. Isolate voice traffic
18. Use proxy servers
19. Run only applications that are necessary to provide and maintain VoIP services
20. Configure applications against misuse
21. Add endpoint security layers
22. Restrict access according to certain criteria
23. Avoid remote management
24. Use IPsec tunneling rather than IPsec transport
25. Secure your VoIP platform
With the help of these cautions, attacks could be lessened and later would be prevented; and the ‘vulnerable’ term to VOIP would be abandoned. With these steps and cautions, network hardware and software requirements should also be considered. Security measures would be useless if the network specifications were poor to accommodate the security demands. Thus, in order to secure VOIP, the network specification should be good enough to serve VOIP services.
Definition and Services of VOIP
Review of Literature
This chapter presents the concepts, facts, and studies related to the present study.
Related Literature
Voice-over-Internet Protocol is an interesting fact that makes a change in the world of telecommunications. It has almost banished the traditional phone lines from the business and home use all over the globe.
Definition and Services of Voice-over-Internet Protocol
VoIP or Voice-over-Internet Protocol is a protocol that makes the transmission of voice via internet connection possible or to other networks which uses packet switching method. It works through broadband and uses the internet to direct its calls. Packet – switching works in sending data packets through a network down into thousands of possible paths. VoIP converts the voice signal from the caller into digital signal before the recipient answers the call.
According on an internet site, (http://www.whichvoip.com/voip/articles/voip_ history.htm) VoIP technology begun in the mid 90’s when the Voltech Company released the software called Internet Phone which was designed to run on a home PC and uses the H.323 protocol instead of an SIP (Session Initiation Protocol) protocol that is used today; and was utilized by a microphone, which is commonly called headphone today, speakers and sound cards. This software represents as the first internet phone.
The site (http://en.wikipedia.org) held, VoIP transmit telephone calls over the same broadband connection. It has advanced telephony features such as call routing, screen pops and IVR implementation. VoIP are portable and work in any location with strong broadband signals and connections; and can access a phone line from many places. VoIP offers unlimited local and international calls with a fixed price; and can allow the consumer to have more than one phone number. There is almost zero charge for its conference calls, call forwarding, automatic redial, and caller IDs.
VoIP is an interesting technology with interesting services. The common services it offers are the following from the site (http://communication.howstuffworks.com/ip-telephony11.htm):
1. ATA (Analog Telephone Adaptor)
2. IP Phones
3. Computer to Computer
The first service allows connecting the ordinary telephone to the computer with internet connection in order to use VoIP. ATA converts the analog signal into digital signal before it is being sent over the internet. The IP phones are specialized phones for use with IP calls. It uses RJ-45 Ethernet connector which connects directly to the internet router and has the necessary software and hardware devices that enable an IP call. The VoIP service over computer-to-computer is the easiest way to use VoIP as long as the in internet connection is present; and the necessary hardware equipments are present such as the microphone, speakers and sound cards. Call cost is totally free no matter the distance in this type of VoIP service.
But there is also a limitation with the services offered by VoIP. According on the site, (http://www.onguardonline.gov/topics/ voip.aspx) in VoIP, there is no need to change for another phone number when the consumer wanted to keep its old regular phone number; but the processing is time costly. Temporarily, the consumer will take the option of using a new phone number. However, Phone numbers of VoIP is not included in a telephone directory listing unlike with that of a telephone registered to a local phone company. Thus, the VoIP user does not have an access to any directory assistance service.
With VoIP service, it is possible to call to an ordinary telephone connected to an adaptor, to a special VoIP phone, or directly from the computer to another computer. With that, anyone can call the number from any regular phone without using any special software and equipment.
Finally, from an internet site, (http://articles.directorym.com/VoIP_Phone_ Service_Vermont-r800278-Vermont.html#8001277) whether the computer is turned off, as long as the connection in the internet is active, VoIP is still available for access and usage. Whether in travel, VoIP can also be in use as long as the adapter or the special software and hardware is present, and the connection to the internet is activated.
This chapter presents the concepts, facts, and studies related to the present study.
Related Literature
Voice-over-Internet Protocol is an interesting fact that makes a change in the world of telecommunications. It has almost banished the traditional phone lines from the business and home use all over the globe.
Definition and Services of Voice-over-Internet Protocol
VoIP or Voice-over-Internet Protocol is a protocol that makes the transmission of voice via internet connection possible or to other networks which uses packet switching method. It works through broadband and uses the internet to direct its calls. Packet – switching works in sending data packets through a network down into thousands of possible paths. VoIP converts the voice signal from the caller into digital signal before the recipient answers the call.
According on an internet site, (http://www.whichvoip.com/voip/articles/voip_ history.htm) VoIP technology begun in the mid 90’s when the Voltech Company released the software called Internet Phone which was designed to run on a home PC and uses the H.323 protocol instead of an SIP (Session Initiation Protocol) protocol that is used today; and was utilized by a microphone, which is commonly called headphone today, speakers and sound cards. This software represents as the first internet phone.
The site (http://en.wikipedia.org) held, VoIP transmit telephone calls over the same broadband connection. It has advanced telephony features such as call routing, screen pops and IVR implementation. VoIP are portable and work in any location with strong broadband signals and connections; and can access a phone line from many places. VoIP offers unlimited local and international calls with a fixed price; and can allow the consumer to have more than one phone number. There is almost zero charge for its conference calls, call forwarding, automatic redial, and caller IDs.
VoIP is an interesting technology with interesting services. The common services it offers are the following from the site (http://communication.howstuffworks.com/ip-telephony11.htm):
1. ATA (Analog Telephone Adaptor)
2. IP Phones
3. Computer to Computer
The first service allows connecting the ordinary telephone to the computer with internet connection in order to use VoIP. ATA converts the analog signal into digital signal before it is being sent over the internet. The IP phones are specialized phones for use with IP calls. It uses RJ-45 Ethernet connector which connects directly to the internet router and has the necessary software and hardware devices that enable an IP call. The VoIP service over computer-to-computer is the easiest way to use VoIP as long as the in internet connection is present; and the necessary hardware equipments are present such as the microphone, speakers and sound cards. Call cost is totally free no matter the distance in this type of VoIP service.
But there is also a limitation with the services offered by VoIP. According on the site, (http://www.onguardonline.gov/topics/ voip.aspx) in VoIP, there is no need to change for another phone number when the consumer wanted to keep its old regular phone number; but the processing is time costly. Temporarily, the consumer will take the option of using a new phone number. However, Phone numbers of VoIP is not included in a telephone directory listing unlike with that of a telephone registered to a local phone company. Thus, the VoIP user does not have an access to any directory assistance service.
With VoIP service, it is possible to call to an ordinary telephone connected to an adaptor, to a special VoIP phone, or directly from the computer to another computer. With that, anyone can call the number from any regular phone without using any special software and equipment.
Finally, from an internet site, (http://articles.directorym.com/VoIP_Phone_ Service_Vermont-r800278-Vermont.html#8001277) whether the computer is turned off, as long as the connection in the internet is active, VoIP is still available for access and usage. Whether in travel, VoIP can also be in use as long as the adapter or the special software and hardware is present, and the connection to the internet is activated.
Research: Significance and Objectives of the Study
Significance of the Study
The research study could provide information on the issues of Voice-over-Internet Protocol technology particularly on the integrity, vulnerability and security of VoIP calls.
Further, this study would also be a review on the VoIP Technology present and service providers based in the Philippines particularly in local Davao City area.
This study would be beneficial to the Commission on Telecommunication in the city as this study enhance the knowledge of the telephony providers and users about the possible issues on VoIP Technology.
Furthermore, this study would be beneficial to the telephony providers and the users as this study would provide the necessary information on the different threats and attacks in VoIP technology. This would expectedly heighten the awareness of the providers and the users to equip a counterattack to possible threats.
To the future researchers, this study can provide baseline information on the recent status of VoIP technology.
Objectives of the Study
This study aimed to determine the issues on the integrity, vulnerability, and security of phone call in VoIP Technology.
This study is designed to identify the possible types of attacks and threats on VoIP Technology and its measures.
This study would specifically persuade the following objectives:
1. To determine the integrity of phone call from Voip Phones
2. To determine the vulnerability of VoIP Phone calls
3. To determine the types of attacks from Voip phone calls.
4. To determine the measures of security from phone call attacks.
5. To realize awareness on VoIP services and issues to the future users.
Research: Introduction
Situational Analysis
In today’s global change in technology, every individual depends on things to make almost everything possible and easy in a fastest and effective way especially when communication is on hand.
Decades back, telephone is most commonly used for landline long distance communication which uses phone switching technology. Then mobile phone was introduced with dual functionality; for text messaging and voice calls. The internet also offers chatting and instant messaging communication; and even internet-to-internet voice chat with the utilization of headphones, sound cards and speakers.
To satisfy the demand of technology, VoIP (Voice over Internet Protocol) technology was introduced to make PC-to-PC connection possible; and later phone-to-phone connection that change the traditional telephony into IP telephony. According on the site (http://www.roseindia.net/voip/voip-history.shtml), VoIP works through broadband technology and uses the World Wide Web to direct its calls.
Though VoIP come out to the market, only few are knowledgeable of it. Many individuals have not heard of VoIP and its functions. It had been out in the business world since prepaid calling cards were introduced. Caller IDs used VoIP technology which is present in telephones used in homes and businesses today. Call centers are one of the user and providers of VoIP.
Many VoIP providers offer the use of VoIP technology and other telecommunication services with VoIP applications. Telecommunication industry is wide spreading. Phones with VoIP are commonly in used; but consumers were not aware of the issues related to the VoIP technology.
Since, Voip uses internet in order to function and deliver voice messages to various recipients. Depending on the internet means depending to the power of electricity. If there is a power outage, which means there, is no VoIP; and this instance can hinder VoIP call integrity and security. Internet nowadays is an attack-prone to hackers and also VoIP. Hacking the internet can make VoIP vulnerable to this attackers and threats; and is more prone to not secure phone calls and voice messages.
Further, attackers and threats may come everywhere at any given time; geniuses which past-time is to prank someone over the internet and send messages that are believable to the victims. Others use codes to implement hacking to one’s privacy; and some interrupt the connection between the caller and the recipient.
Consider the political intrigue the Philippine President got into during the 2004 presidential elections. The Presidential call was wire-tapped and was recorded; and later was engaged in controversy and was familiarized by the Filipino masses as the “Hello Garci” scandal. VoIP also can be picture-out like this.
Thus, it is important to provide adequate information in the context of awakening the community about VoIP and its related issues.
However, in propelling this opportunity, further reading is required; and research is essential.
Decades back, telephone is most commonly used for landline long distance communication which uses phone switching technology. Then mobile phone was introduced with dual functionality; for text messaging and voice calls. The internet also offers chatting and instant messaging communication; and even internet-to-internet voice chat with the utilization of headphones, sound cards and speakers.
To satisfy the demand of technology, VoIP (Voice over Internet Protocol) technology was introduced to make PC-to-PC connection possible; and later phone-to-phone connection that change the traditional telephony into IP telephony. According on the site (http://www.roseindia.net/voip/voip-history.shtml), VoIP works through broadband technology and uses the World Wide Web to direct its calls.
Though VoIP come out to the market, only few are knowledgeable of it. Many individuals have not heard of VoIP and its functions. It had been out in the business world since prepaid calling cards were introduced. Caller IDs used VoIP technology which is present in telephones used in homes and businesses today. Call centers are one of the user and providers of VoIP.
Many VoIP providers offer the use of VoIP technology and other telecommunication services with VoIP applications. Telecommunication industry is wide spreading. Phones with VoIP are commonly in used; but consumers were not aware of the issues related to the VoIP technology.
Since, Voip uses internet in order to function and deliver voice messages to various recipients. Depending on the internet means depending to the power of electricity. If there is a power outage, which means there, is no VoIP; and this instance can hinder VoIP call integrity and security. Internet nowadays is an attack-prone to hackers and also VoIP. Hacking the internet can make VoIP vulnerable to this attackers and threats; and is more prone to not secure phone calls and voice messages.
Further, attackers and threats may come everywhere at any given time; geniuses which past-time is to prank someone over the internet and send messages that are believable to the victims. Others use codes to implement hacking to one’s privacy; and some interrupt the connection between the caller and the recipient.
Consider the political intrigue the Philippine President got into during the 2004 presidential elections. The Presidential call was wire-tapped and was recorded; and later was engaged in controversy and was familiarized by the Filipino masses as the “Hello Garci” scandal. VoIP also can be picture-out like this.
Thus, it is important to provide adequate information in the context of awakening the community about VoIP and its related issues.
However, in propelling this opportunity, further reading is required; and research is essential.

 Let us support FOSS!
Let us support FOSS!But what is FOSS?
According to wikipedia.com, FOSS stands for Free and open source software, "is software which is liberally licensed to grant the right of users to study, change, and improve its design through the availability of its source code."
That's FOSS and let's indulged with it!
Subscribe to:
Comments (Atom)


